The Evolution of Integrity: From Blind Hashes to Visual Truth
Traditional hashing is a binary yes/no. VFP adds a third dimension: visual context. Explore how we transform blind mathematical strings into structural landscapes.
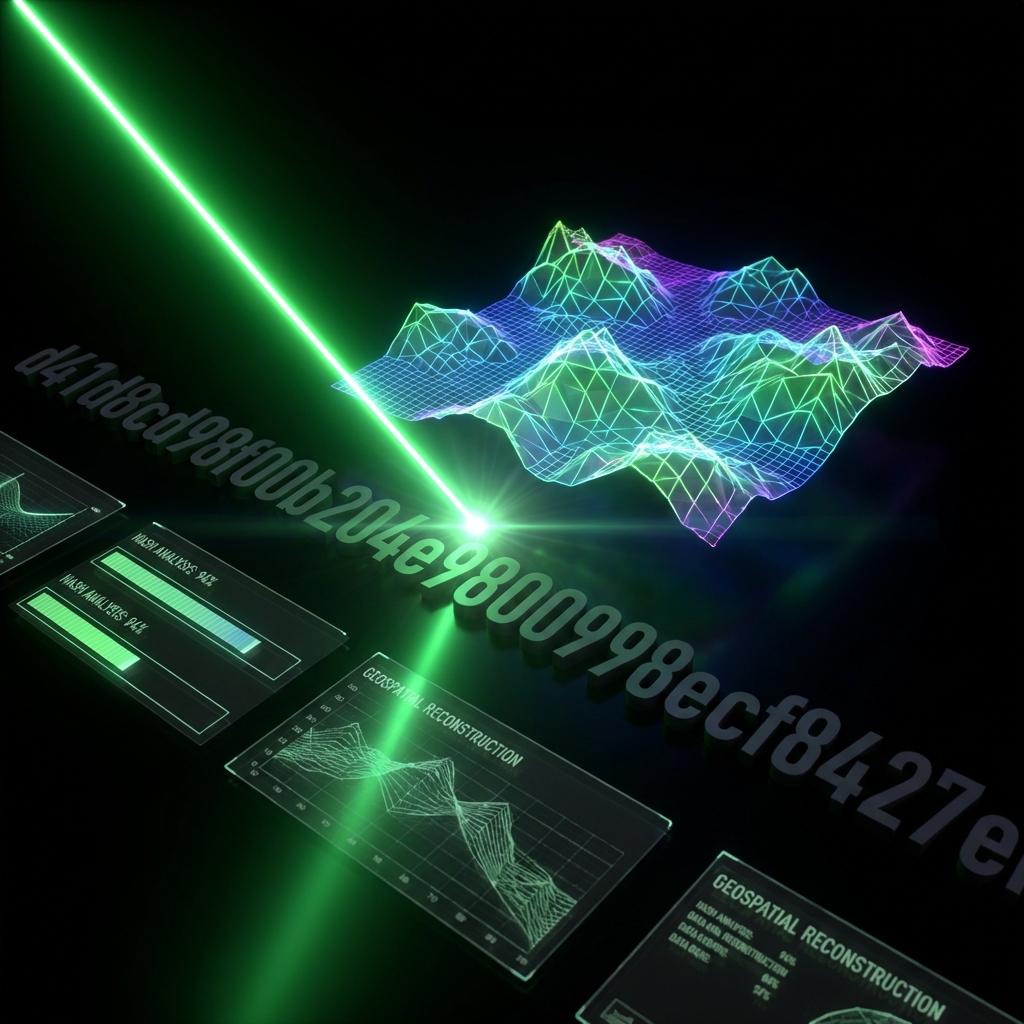
For decades, the standard for digital integrity has been the cryptographic hash. Whether MD5, SHA-1, or SHA-256, the logic was the same: if a single bit flips, the entire string changes. But what if the string doesn't tell you enough?
The Limitations of Blind Verification
Traditional hashing is essentially a blind gatekeeper. It can tell you that a file has been modified, but it cannot tell you where, how, or why. For a security operator managing petabytes of data, a "hash mismatch" is a nightmare—it signals a problem without providing a roadmap to the solution.
"VFP doesn't replace the Hash; it gives it eyes. It transforms a blind verification into a multidimensional diagnostic."
Entering the Visual Domain
VFP (Visual Fingerprint Protocol) introduces the concept of structural topography. By mapping binary data into the Hilbert Plane and applying the 7D Lens Matrix, we create a "skin" for your data. This skin reflects the internal state of the file. A malware injection isn't just a hash error; it's a visible topographical anomaly—a jagged peak in a forest of predictable patterns.
The Hybrid Future
Aegis NextGen advocates for a "VFP-First" strategy. We use hashing for rapid identity confirmation and VFP for deep structural validation. Together, they form the most robust integrity framework ever developed for the enterprise.
